In a well-known episode of the sitcom Seinfeld, the character George Costanza, when his fiancée Susan becomes friends with Elaine Benes, part of the circle of friends centered around Jerry Seinfeld who are the focus of the show, responds by shouting, “Worlds are colliding!” I felt much the same way earlier this week as the Catholic publication The Pillar‘s exposé of Msgr. Jeffrey Burrill’s use of the gay hookup app Grindr received coverage in the secular tech media and even gained the attention of U.S. Senator Ron Wyden, one of only a few serious advocates for strong digital privacy on Capitol Hill.
I have long had an interest in exploring from a theological perspective the ethical and anthropological issues raised by digital and internet technologies, and recently I have written quite a bit on how Catholic ethics can inform discussions of digital privacy and cybersecurity. I have even been working on and off on what might become a textbook on Catholic ethics and, for lack of a better term, digital information ethics. In order to keep abreast of new developments in this field in which I am by no means a specialist and to inform my own work as a theologian, I follow several tech journalists, activists, and cybersecurity experts on social media.
I was surprised, though, that the buzz in the tech world this week, what one expert in digital privacy calls a “hugely significant” event that makes manifest privacy issues advocates “have been screaming from the rooftops [about] for years,” would involve a case raising the problem of moral accountability in the Catholic Church at a time when the Church has been rocked by years of scandal and prevarication from its leadership. Whereas George Costanza’s response to his worlds colliding was frustration and anger, our response to the case of Msgr. Burrill should be to recognize not only the urgency of moral accountability among the leaders of the Church, but also the role that digital privacy issues will play in our efforts to implement this accountability, issues that Catholics have neglected for too long. Before looking at those urgent moral problems, however, I think it is important to look in detail at the facts we have available about this case. If we get the facts wrong or if we lack crucial facts, we may get our moral analysis wrong. I will return to these moral problems in a later post.
What happened?
Although The Pillar‘s exposé has been summarized elsewhere (in addition to the articles by Motherboard and Ars Technica linked above, also see the report in the Washington Post), it is worth summarizing here because I want to explore some of the key points in more detail. The Pillar, a Substack written by the Catholic journalists JD Flynn and Ed Condon, alleges that Msgr. Burrill, until this past Tuesday the general secretary of the United States Conference of Catholic Bishops (USCCB), had engaged in “serial sexual misconduct.” The Pillar describes the basis of this allegation in this way:
[A]n analysis of app data signals correlated to Burrill’s mobile device shows the priest also visited gay bars and private residences while using a location-based hookup app in numerous cities from 2018 to 2020, even while traveling on assignment for the U.S. bishops’ conference.
According to commercially available records of app signal data obtained by The Pillar, a mobile device correlated to Burrill emitted app data signals from the location-based hookup app Grindr on a near-daily basis during parts of 2018, 2019, and 2020 — at both his USCCB office and his USCCB-owned residence, as well as during USCCB meetings and events in other cities.
Before publishing the exposé, The Pillar presented their findings to the USCCB, which led to Burrill’s resignation on July 20.
What is Grindr, and what happens to data collected by the app?
Grindr is a social networking app marketed to gay men and primarily used to facilitate sexual encounters or hook ups, although some users use it to initiate longer-term relationships. A member creates a profile which includes a picture and personal information such as sexual preferences. Each member creates a username, but many use a nickname to remain anonymous. When using the app, the member will see the profile picture of other users nearby in order of proximity. The app also shows the distance between the member and other users, although users can turn off this feature (I will explain the reasons for this in the later post). Members can then communicate with one another and share their locations to meet up.

Like most apps, Grindr collects users’ data, including not just data the user enters directly into the app, but also data pulled from their phone or computer. Most importantly, Grindr pulls users’ GPS location data from their phones, which the app then uses to identify the location of the user and which other users are nearby. According to Grindr’s privacy policy, this location data is deleted after seven days. That is not the end of the story, however. Again like many other apps, Grindr sells this data to companies called “data brokers” who use it mainly for targeted advertising and market research. Coincidentally, we know a great deal more about the data practices of Grindr than other apps because privacy issues with the app identified by users led the Norwegian non-profit ForbrukerRådet (the Consumer Council) to issue a report on the data practices of Grindr (as well as the dating apps OkCupid and Tinder and a number of other apps). The report found that Grindr passes users’ data to unfamiliar companies such as MoPub (owned by Twitter), AppNexus (owned by AT&T), Bucksense, OpenX, PubNative, Vungle, AdColony, and Smaato. These vendors in turn sell the data to countless other companies, mostly advertisers. In many cases these transactions are used to generate targeted advertisements in the Grindr app itself, but in others the data is used to generate targeted advertisements for other apps or web sites or for general market research.
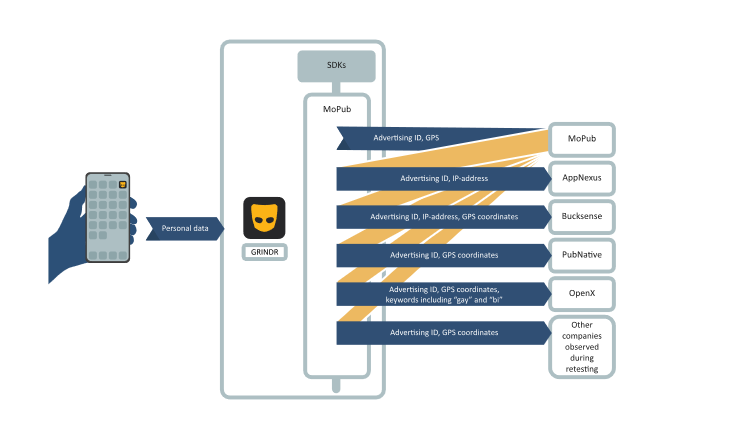
Although apps like Grindr do not share users’ personal information like their names and phone numbers (in other words, the data is “anonymized”), it is nevertheless relatively easy for data brokers and ad vendors to create personal profiles for individuals. For example, apps collect a user’s IP address, the unique identifier assigned to a device or network that communicates where data should be sent across the internet (it is somewhat like your street address on the internet). Therefore, data brokers can create a consumer profile of all the data collected from the devices using your home network’s public IP address. This also explains why this spring, when I was researching on my home computer before purchasing a new lawnmower, I started to see advertisements for lawnmowers on the Facebook app on my phone! Some data brokers also create what are called mobile advertising IDs, number used to identify data collected from a single individual. Individual data can be “de-anonymized” by linking an IP address to a specific person’s device or using GPS location data that identifies likely home addresses or workplaces.
The de-anonymizing of personal data might be unproblematic if it was only used for targeted advertising. The ability to tailor ads to people’s personal interests benefits both advertisers and consumers. But once data is commodified, it is difficult to regulate to whom it can be sold. As Motherboard recently reported, some data brokers have now begun selling personalized data sets called “identity resolutions” or “identity graphs” that link mobile advertising IDs with personal information such as names and addresses. Although these products are primarily marketed to advertisers, Motherboard has also uncovered how data brokers have also been selling personal data originally sold by telecom companies to bounty hunters, debt collectors, and others, either on the black market or through deception on the part of the buyers. In one case a stalker impersonating a US Marshal bought his victim’s location data from T-Mobile. The police and other law enforcement agencies can also access people’s personal data. In many cases law enforcement will get a warrant to obtain access to data, including web histories and search histories, from telecom companies, but law enforcement agencies have also started purchasing the data from data brokers, bypassing the need for a warrant.
How did The Pillar obtain data from Grindr, and what kind of data did they obtain?
As noted above, The Pillar says that they “obtained” “commercially available records of app signal data,” but they do not explain how they obtained the data or from whom. The day before the exposé was released, however, the Catholic News Agency curiously reported on the “prospect of private parties using national security-style surveillance technology to track the movements and activities of bishops, priests, and other Church personnel,” noting that “there are reports this week that information targeting allegedly active homosexual priests may become public.” The report goes on to say:
The issue was first raised in 2018, when a person concerned with reforming the Catholic clergy approached some Church individuals and organizations, including Catholic News Agency.
This party claimed to have access to technology capable of identifying clergy and others who download popular “hook-up” apps, such as Grindr and Tinder, and to pinpoint their locations using the internet addresses of their computers or mobile devices.
The proposal was to provide this information privately to Church officials in the hopes that they would discipline or remove those found to be using these technologies to violate their clerical vows and possibly bring scandal to the Church. …
CNA also spoke with some Catholics who were originally approached in 2018.
Like CNA, they were offered specific names of high-profile Catholic personalities as “proof” that the data had been gathered and could prove scandalous.
The party presenting the data claimed to have the best interest of the Church at heart in offering the data to Catholics. He voiced fears that such information could wind up in “the wrong hands,” and be used to blackmail Church officials or otherwise hurt the Church.
Although not certain, the evidence (including the specific reference to Grindr, the use of location data, and the intention of uncovering scandalous behavior) suggests this unnamed person was the source of the data obtained by The Pillar. But how did this person get access to the data? They may own or work for a data brokerage. They may have purchased the data from a data broker. The Catholic writer Dawn Eden Goldstein has compiled an intriguing list of Catholics involved in the data industry or who have been involved in collecting digital data on Catholics and who may have had an interest in exposing scandalous behavior among church leaders, although without further evidence these are merely speculations.
Although it remains unknown who first obtained the data on Msgr. Burrill, I believe there is clearer evidence on what kind of data was shared with The Pillar. Here is how The Pillar describes the data, in three separate sections of the article:
According to commercially available records of app signal data obtained by The Pillar, a mobile device correlated to Burrill emitted app data signals from the location-based hookup app Grindr on a near-daily basis during parts of 2018, 2019, and 2020 — at both his USCCB office and his USCCB-owned residence, as well as during USCCB meetings and events in other cities. …
On June 20, 2018, the day the McCarrick revelations became public, the mobile device correlated to Burrill emitted hookup app signals at the USCCB staff residence, and from a street in a residential Washington neighborhood. He traveled to Las Vegas shortly thereafter, data records show.
On June 22, the mobile device correlated to Burrill emitted signals from Entourage, which bills itself as Las Vegas’ “gay bathhouse.” …
The Pillar correlated a unique mobile device to Burrill when it was used consistently from 2018 until at least 2020 from the USCCB staff residence and headquarters, from meetings at which Burrill was in attendance, and was also used on numerous occasions at Burrill’s family lake house, near the residences of Burrill’s family members, and at a Wisconsin apartment in Burrill’s hometown, at which Burrill himself has been listed as a resident.
Based on this reporting and the description of Grindr’s data practices reported by ForbrukerRådet that I mentioned earlier, it seems highly likely to me that that the data is GPS location data or some derivative of it. In other words, the Grindr app collected GPS location data from Burrill’s phone, this data was sold to multiple data brokers, and through some unknown chain this data ended up in the hands of The Pillar. If this is true, however, then it seems likely to me that The Pillar has presented the data in a misleading way, although probably unintentionally so based on a misunderstanding of the data they had on hand. Note how in the passages cited above the data is repeatedly referred to as “emitted app data signals” or “emitted hookup app signals” originating from a variety of locations, including the the USCCB headquarters, an apartment identified as Burrill’s residence, a family lake house, and the residences of various family members, but also including a gay bathhouse in Las Vegas. This suggests that the data was produced by Burrill’s use of the app in those locations. This suggestion is reinforced by the report’s allegation that “Data app signals suggest he was [at the same time he was employed at the USCCB] engaged in serial and illicit sexual activity” (emphasis added), and, in the passage cited at the beginning of this post, that ” Burrill emitted app data signals from the location-based hookup app Grindr on a near-daily basis.” But if I am correct that the data is simply GPS location data, then it tells us nothing at all about where, how, or when Burrill used Grindr. All it tells us is the places where he had his cell phone on, information that was indiscriminately collected by the Grindr app and then sold to third parties.
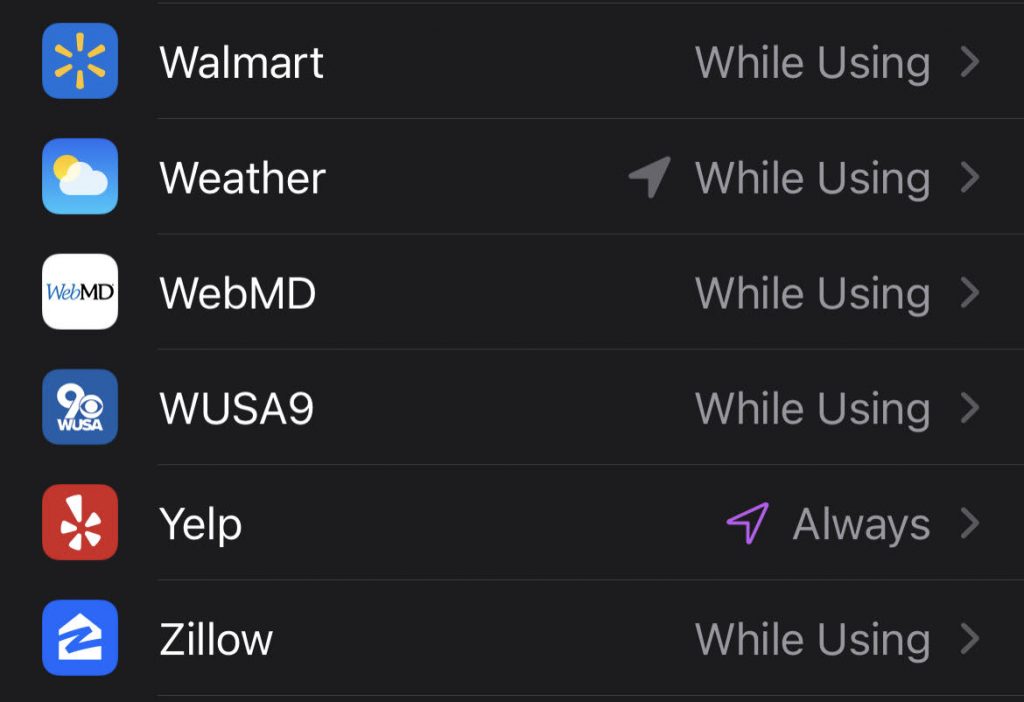
Let me explain a bit further. As I noted earlier, many apps are designed to collect GPS location data, usually because the data is necessary for some feature of the app. For example, on my own iPhone, the Weather app collects my location data to provide me with the weather forecast in my current location, the Yelp app collects it to recommend nearby restaurants, and the Walmart app uses it to point me toward the nearest Walmart store. iPhones and Android phones let users specify whether they want to allow apps to always track their location, to track it only when they are using the app, to ask before tracking their location, or to disallow location tracking altogether (the latter of which would hinder the functionality of many apps). I usually allow apps to track my location only when I am using them, but I have temporarily set Yelp to always track my location for illustration purposes. If I kept that setting turned on, then Yelp would have data on all the places I go, regardless of whether I use Yelp in those locations or not.
I believe this is the most likely origin of the data analyzed by The Pillar: Burrill, probably unaware, had Grindr set to always track his location, and the app therefore collected data on the places he traveled, most of which was likely innocent, everyday activity. It is certainly possible that I am incorrect and that the data analyzed by The Pillar does indeed show “serial” use of the Grindr app in some pretty unusual locations, but in my view that remains unlikely without further evidence.
This is not at all meant as an exoneration of Msgr. Burrill. The very fact thats he had the Grindr app installed on his phone from at least 2018 to 2020 and that in 2018 he visited a gay bathhouse suggest that he did engage in misconduct. But a close look at the available data suggests we know far less about Burrill’s conduct than initially thought.
How was Msgr. Burrill personally identified?
This close look also suggests how Msgr. Burrill’s personal data may have been identified in the first place. In an analysis of the situation published at America, Zac Davis asks, ” Why was Monsignor Burrill investigated in the first place? It matters whether he was intentionally targeted or whether his actions came to light in the course of a wider search.” Put another way, has someone collected data on church leaders in the hope of finding something scandalous, or was the data of specific clerics targeted because of suspicions aroused by other means? In his own analysis also published at America, Sam Sawyer, S.J., likewise states, ” [T]here are … a number of methodological questions about how the data analysis itself was conducted, and how that analysis led to Monsignor Burrill specifically.” Some of Sawyer’s thoughts are worth citing in detail:
There are, indeed, commercially available datasets of cellphone location data. One such dataset is marketed as containing 59.4 billion monthly pings covering 275 million monthly active users. But how do you go about extracting a single needle, correlated to one priest’s smartphone, out of such a potentially enormous haystack? …
… There are two basic ways to start [personally identifying someone using location data]. You can either start with some names—proposed targets for investigation—and try to find the devices belonging to them by using their known addresses and travel patterns, then follow their dotted lines to look at where else they’ve been. Or you can start with some significant locations and look at all the dotted lines going through those dots. Then, when you find a line that’s doing something or going somewhere it shouldn’t, you look at its consistent patterns of travel to connect that device to some specific person.
The available evidence suggests to me that the latter is the more likely possibility. Here is one possible scenario: Based on the Catholic News Agency’s reporting concerning a person with data on priests engaged in scandalous behavior cited above (and assuming this person is indeed the source for the data, which, as I said, seems likely), this person claims to have had data obtained from users of Grindr (location data, but possibly other types of data, as well). The person then searched this location data for (at this point anonymous) users who had visited a specific location, such as the USCCB office in Washington, DC (much like the New York Times was able to identify 130 individuals who were inside the U.S. Capitol during the January 6 insurrection). As a result, the person was able to identify a small number of anonymous Grindr users who had proximity to the USCCB. The identity of these individuals could then be discovered by using the IP address of their phone or some other identifier to trace other locations they frequented and checking those locations against address records publicly available on the internet or through other sources. Using this relatively simple method, someone could have personally identified prominent Catholics who had downloaded the Grindr app and traced locations they may have visited, revealing potentially scandalous activity. This is simply one possibility, an educated guess, and I am open to correction if new information emerges, but to my mind this sounds like the simplest way Msgr. Burrill could have been identified.

In this post, I have spent a lot of time exploring the facts of the case, both known and unknown, while setting aside the urgent ethical issues I mentioned at the beginning, both concerning Msgr. Burrill’s conduct and the use of his personal data. I will address these issues in an upcoming post.
Update
In the hours after this post was published, two developments helped confirm my main conclusions about the data used by The Pillar. First, JD Flynn and Ed Condon issued a new episode of The Pillar Podcast discussing the exposé and some of the criticisms that have been made of their work. In the episode, they confirm my supposition about how they singled out Msgr. Burrill: they were handed anonymous location data for numerous individuals who were users of Grindr (and other apps), they focused in on locations of ecclesiastical significance (such as the USCCB headquarters) and identified users who had visited those locations, and then they traced those users to other locations that could be used to personally identify them, like residences. They also seemingly confirmed that a source who had legally purchased the data provided them with the data set, and that The Pillar had not purchased the data themselves, although this is not 100 percent clear. They did not confirm whether the source was the person identified in the Catholic News Agency reporting, and in fact expressed agnosticism about the motives of the source.
Second, The Pillar published a new report using the same technique, focusing on rectories and clerical residences in the Archdiocese of Newark, identifying at least ten residences frequented by users of unspecified “hookup apps,” suggesting that these users are priests of the archdiocese. In this case the journalists did not personally identify the users of the app. Notably, The Pillar continues to conflate location data collected by an app with use of the app in that location, a problem I explained in the post above. In the new report, they claim that the data “shows evidence that both homosexual and heterosexual hookup apps were used in parish rectories or other clerical residences with a frequency suggesting, in several cases, residence in those locations.” If my above analysis is correct, then this data does not show that individuals used the apps in the rectories or clerical residences, only that someone with one of those apps on their phone was present at the rectories or residences. Although the fact that the users were frequently at those locations suggests that they are in fact priests, the data does not rule out the hypothetical possibility that these users are a housekeeper with a dating app on their phone, a frequent visitor, or even a parishioner seeking counsel from a priest regarding sexual temptations. And as with my post above, my point here is not at all to hide the wrongdoing of any priests who were using “hookup apps, but rather to suggest that data can create an illusion of objectivity, leading us to overestimate the information we really possess.




Trackbacks/Pingbacks